The Role of Artificial Intelligence in Enhancing WAPT
Introduction:
Web Application Penetration Testing (WAPT) is a critical component of cybersecurity, ensuring the resilience of web applications against potential cyber threats. As technology evolves, the landscape of cyber threats becomes more sophisticated, necessitating the adoption of advanced tools and techniques. Artificial Intelligence (AI) has emerged as a transformative force in various domains, including cybersecurity. This essay explores the role of AI in enhancing Web Application Penetration Testing, examining its applications, benefits, challenges, and the future prospects of this integration.
“While AI serves as a powerful catalyst for progress in the realm of Web Application Penetration Testing (WAPT), its true essence lies in transforming challenges into opportunities. As the guardian of digital fortresses, AI enhances WAPT by tirelessly exploring vulnerabilities, adapting to evolving threats, and fortifying the security landscape. In the dance between offense and defense, AI orchestrates a symphony of insights, empowering cybersecurity professionals to not only keep pace with adversaries but to stay one step ahead. The role of AI in WAPT is not just about automation; it is a dynamic partnership, an alliance that propels us into a future where security is not a destination but a continuous journey of resilience and adaptability.”
I. Understanding Web Application Penetration Testing:

Before delving into the role of AI, it is essential to grasp the fundamentals of Web Application Penetration Testing.
In an era dominated by digital advancements, web applications have become the lifeblood of businesses, offering convenience and accessibility. However, this digital dependency also opens the door to potential vulnerabilities that malicious actors can exploit. To safeguard sensitive information and ensure the integrity of web applications, organizations turn to a crucial cybersecurity practice: Web Application Penetration Testing.
The Essence of Web Application Penetration Testing
Web Application Penetration Testing, often referred to as ethical hacking or white-hat hacking, is a proactive approach to identify and rectify security weaknesses within web applications. The primary goal is to simulate real-world cyberattacks to discover vulnerabilities before malicious hackers do. This process involves a systematic and thorough examination of the application’s infrastructure, code, and overall security posture.
The Importance of Web Application Security
Web applications are a prime target for cyber threats due to their widespread use and the valuable data they handle. From personal information to financial transactions, web applications store a wealth of sensitive data, making them attractive to hackers seeking unauthorized access. A breach not only jeopardizes user privacy but can also have severe repercussions on a company’s reputation and financial stability.
The Penetration Testing Process
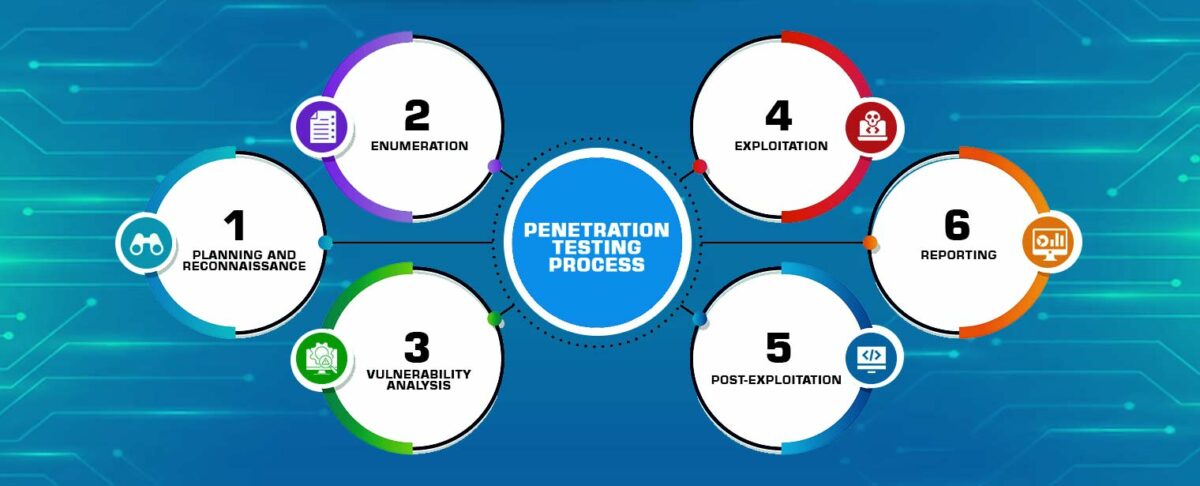
1. Planning and Reconnaissance:
The penetration testing journey begins with meticulous planning and reconnaissance. Testers analyze the target application, identify potential entry points, and gather information about the system’s architecture and technology stack.
2. Enumeration:
This phase involves mapping out the application’s structure, endpoints, and functionality. Testers use various tools and techniques to discover hidden or undocumented features that may harbor vulnerabilities.
3. Vulnerability Analysis:
Here, testers actively search for vulnerabilities by manipulating input fields, injecting malicious code, and scrutinizing the application’s responses. Common vulnerabilities include SQL injection, cross-site scripting (XSS), and insecure direct object references (IDOR).
4. Exploitation:
Once vulnerabilities are identified, the next step is to exploit them. This involves simulating real-world attacks to understand the potential impact and gain unauthorized access to sensitive data or functionalities.
5. Post-Exploitation:
After successful exploitation, testers evaluate the extent of the compromise and assess the effectiveness of existing security measures. This step helps organizations understand the potential consequences of a real cyberattack.
6. Reporting:
A comprehensive report is then generated, detailing the vulnerabilities discovered, the severity of each issue, and recommendations for remediation. This report serves as a roadmap for organizations to enhance their security posture.
Benefits of Web Application Penetration Testing
1. Risk Mitigation:
By identifying and addressing vulnerabilities proactively, organizations reduce the risk of unauthorized access and data breaches.
2. Compliance Assurance:
Many industries have regulatory requirements mandating regular security assessments. Web application penetration testing helps organizations stay compliant with these standards.
3. Reputation Management:
Demonstrating a commitment to security through penetration testing enhances an organization’s reputation, instilling confidence in clients and stakeholders.
4. Cost-Effective Security:
Investing in penetration testing is a cost-effective approach compared to the potential financial losses and reputational damage resulting from a successful cyberattack.
In an interconnected digital landscape, the importance of web application penetration testing cannot be overstated. It is a proactive measure that empowers organizations to stay one step ahead of cyber threats. By identifying and rectifying vulnerabilities before they can be exploited, businesses can ensure the security and integrity of their web applications, safeguarding both their assets and the trust of their users. Embracing web application penetration testing is not just a cybersecurity strategy; it is a commitment to resilience in the face of evolving digital threats.
II. The Need for Advanced Techniques:
Traditional methods of penetration testing often fall short in addressing the dynamic and complex nature of modern web applications. As applications become more intricate, attackers also adapt their strategies, making it challenging for conventional tools to keep up. AI, with its ability to analyze vast amounts of data, recognize patterns, and adapt to evolving threats, offers a promising solution to enhance the efficacy of WAPT.
III. Applications of AI in WAPT:
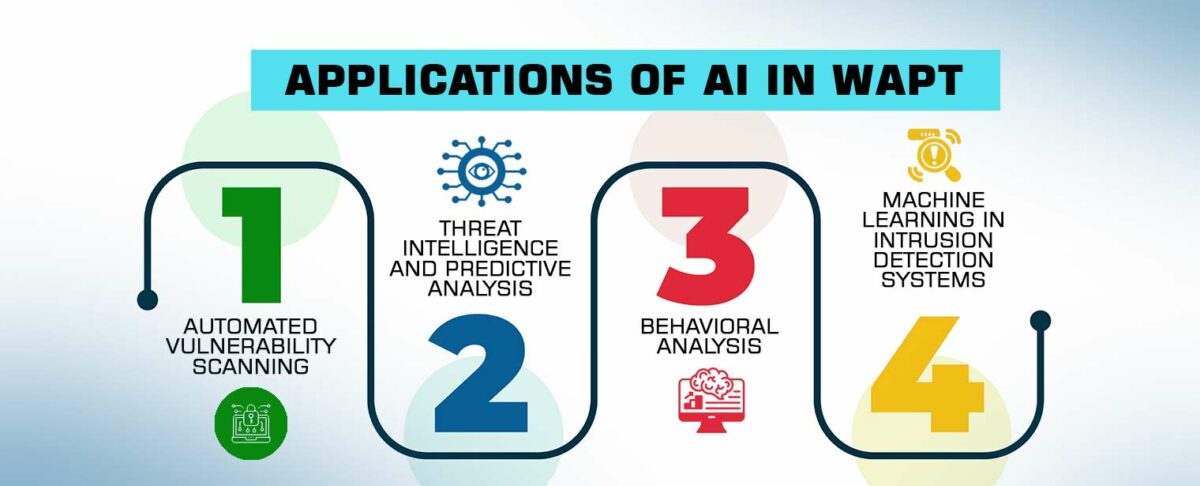
a. Automated Vulnerability Scanning:
One of the significant applications of AI in WAPT is automated vulnerability scanning. AI-powered tools can autonomously scan web applications for potential vulnerabilities, reducing the time and effort required compared to manual methods. These tools leverage machine learning algorithms to identify patterns indicative of vulnerabilities, enabling faster and more accurate detection.
b. Threat Intelligence and Predictive Analysis:
AI can analyze threat intelligence data from various sources to predict potential future attacks. By identifying patterns and correlations in historical data, AI models can provide valuable insights into the types of threats a web application might face. This proactive approach allows organizations to implement preventive measures before vulnerabilities are exploited.
c. Behavioral Analysis:
AI excels in behavioral analysis, which is crucial for detecting anomalous activities within web applications. By establishing a baseline of normal behavior, AI systems can identify deviations that may indicate a security threat. This real-time monitoring enhances the ability to detect and respond to attacks promptly, minimizing potential damage.
d. Machine Learning in Intrusion Detection Systems:
Intrusion Detection Systems (IDS) play a crucial role in WAPT by monitoring network and system activities for signs of unauthorized access or malicious activities. AI, particularly machine learning algorithms, enhances IDS capabilities by learning from historical data and adapting to new attack patterns. This dynamic approach improves the accuracy of intrusion detection and reduces false positives.
IV. Benefits of AI in WAPT:
a. Efficiency and Speed:
AI-driven WAPT tools significantly improve the efficiency and speed of the testing process. Automated vulnerability scanning and analysis can cover large and complex web applications more comprehensively and quickly than manual methods. This acceleration is crucial in the context of rapidly changing cyber threats.
b. Enhanced Accuracy:
The ability of AI to analyze vast datasets and identify subtle patterns enhances the accuracy of vulnerability detection. This reduces the likelihood of false positives and negatives, providing organizations with more reliable insights into the security posture of their web applications.
c. Continuous Monitoring:
AI facilitates continuous monitoring of web applications, allowing organizations to stay vigilant against evolving threats. Unlike periodic manual testing, AI-driven tools can operate in real-time, providing a continuous assessment of the security status and enabling proactive response to emerging vulnerabilities.
d. Adaptability to Evolving Threats:
The dynamic nature of cyber threats requires a corresponding level of adaptability in security measures. AI excels in adapting to new and emerging threats by learning from past incidents and continuously updating its knowledge base. This adaptability is crucial in a landscape where attackers constantly innovate their tactics.
V. Challenges and Considerations:
While the integration of AI in WAPT brings substantial benefits, it is not without challenges and considerations.
a. False Positives and Negatives:
AI models, particularly in the early stages of implementation, may produce false positives or negatives. This can result from the complexity of web applications and the diversity of potential attack vectors. Organizations must carefully validate and fine-tune AI models to minimize inaccuracies.
b. Limited Understanding of Context:
AI systems may lack the contextual understanding that human penetration testers possess. While AI excels in pattern recognition, it may struggle to interpret the broader context of certain vulnerabilities. Human expertise remains crucial in comprehending the intricacies of specific web applications and business processes.
c. Adversarial Attacks:
Adversarial attacks involve manipulating AI systems by exploiting their vulnerabilities. In the context of WAPT, attackers might attempt to deceive AI-powered tools by crafting attacks specifically designed to evade detection. Continuous research and development are essential to fortify AI models against such adversarial tactics.
d. Ethical Considerations:
The use of AI in WAPT raises ethical considerations, particularly regarding privacy and data protection. Organizations must ensure that AI-driven testing tools adhere to ethical standards, respecting user privacy and safeguarding sensitive information.
VI. Future Prospects:
The integration of AI in WAPT is an evolving field with significant potential for future advancements.
a. Improved Human-AI Collaboration:
The future of WAPT likely involves a more seamless collaboration between human penetration testers and AI systems. While AI can automate routine tasks and enhance efficiency, human expertise remains critical for interpreting results, understanding context, and making informed decisions.
b. Integration with DevSecOps:
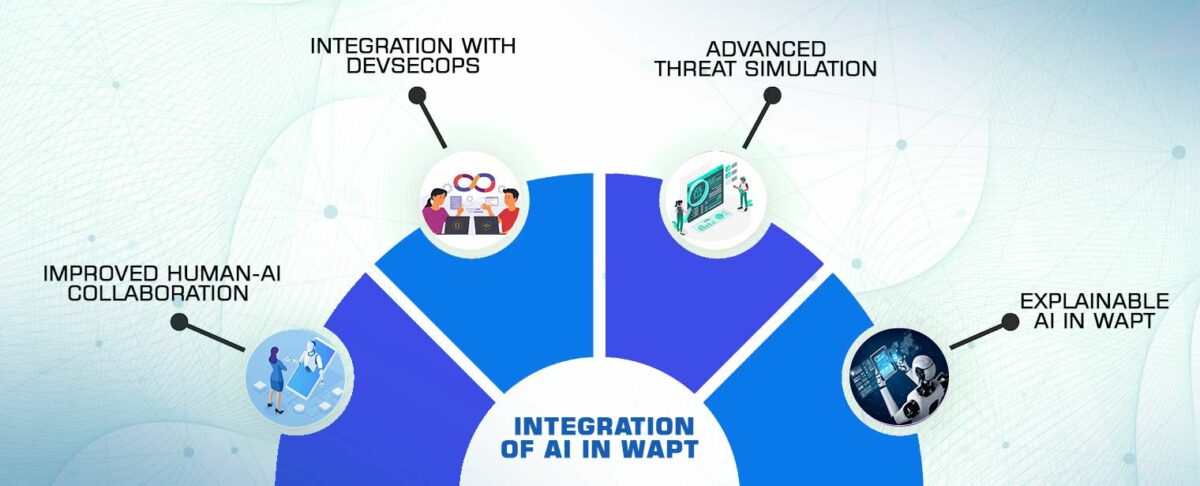
As organizations embrace DevSecOps practices, the integration of AI in WAPT becomes even more pivotal. AI can play a central role in automating security testing within the development lifecycle, providing real-time feedback to developers and fostering a proactive approach to security.
c. Advanced Threat Simulation:
AI-powered tools may evolve to simulate more advanced and sophisticated cyber threats, allowing organizations to test their web applications against realistic scenarios. This advanced threat simulation can provide a more accurate assessment of a web application’s resilience against determined and resourceful adversaries.
d. Explainable AI in WAPT:
Explainable AI (XAI) is an area of research focused on making AI models more transparent and interpretable. In WAPT, the adoption of XAI can address concerns related to the lack of understanding of AI decisions. Providing clear explanations for vulnerability assessments enhances the trustworthiness of AI-driven testing tools.
Conclusion:
The integration of AI in Web Application Penetration Testing represents a significant leap forward in enhancing cybersecurity capabilities. AI-driven tools bring efficiency, accuracy, and adaptability to the testing process, enabling organizations to better defend their web applications against evolving cyber threats. While challenges exist, ongoing research, collaboration between human experts and AI, and a commitment to ethical practices will contribute to the continued success of AI in WAPT. As technology advances, the symbiotic relationship between AI and cybersecurity will play a crucial role in ensuring the resilience of web applications in an ever-changing digital landscape.
